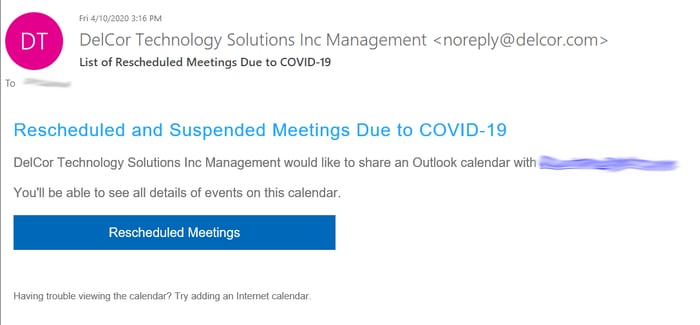
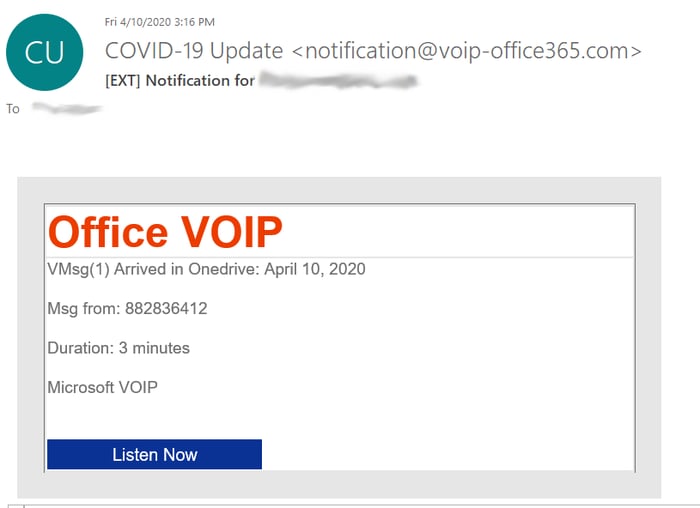
According to InfoSecurity Magazine, phishing emails spiked by 667% in March. Cybercriminals have taken advantage of the panic and insecurity generated by the global pandemic, using social engineering attacks to solicit sensitive information and extort targets. In addition to the typical social engineering attacks, cybercriminals are now using COVID-19 information to prey on vulnerable users.
To protect your organization, it’s crucial to educate staff members on social engineering attacks—especially as those attacks have become more sophisticated every day since this crisis started.
KnowBe4 You Click
As part of our Partner Support program, we offer security awareness training and testing for partner clients. We provide security training for our association and nonprofit clients using KnowBe4—the world’s largest security awareness training and simulated phishing platform.
Using KnowBe4, we train and phish users, track the percentage of success, and enable organizations learn from the results. This platform is so effective because we are able to customize the simulations to help our partner clients handle social engineering attacks that are specific to associations and nonprofits.
Social Engineering Attack Examples
Phishing – attempting to acquire sensitive information (e.g., usernames, passwords, credit card details) by masquerading as a trustworthy entity using bulk email that tries to evade spam filters
Spear phishing – professional phishing targeted at a specific individual based on research
Session hijacking – hacking web sessions to steal information
CEO fraud – phishing disguised as correspondence from a company executive to an employee
Ransomware – denying access to a device or file until a ransom has been paid
When client staff members are tested with simulated email phishing campaigns, we are able to track the reaction of the staff, offer recommendations for improvement, and watch their percentage of success improve over time.
Given the flexibility of the KnowBe4 platform, we are able to use COVID-19 templates to train our clients to avoid coronavirus-specific phishing. The following are real-world examples of phishing emails that KnowBe4 turned into templates to simulate a COVID-19 social engineering attack:
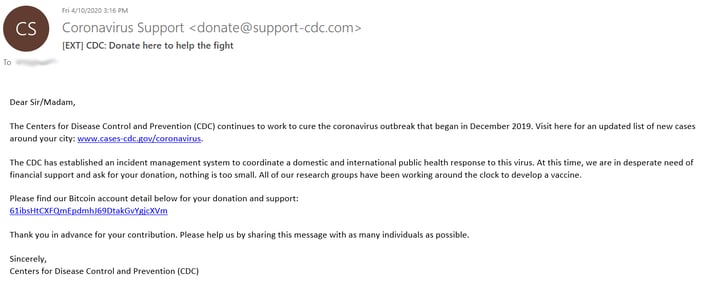
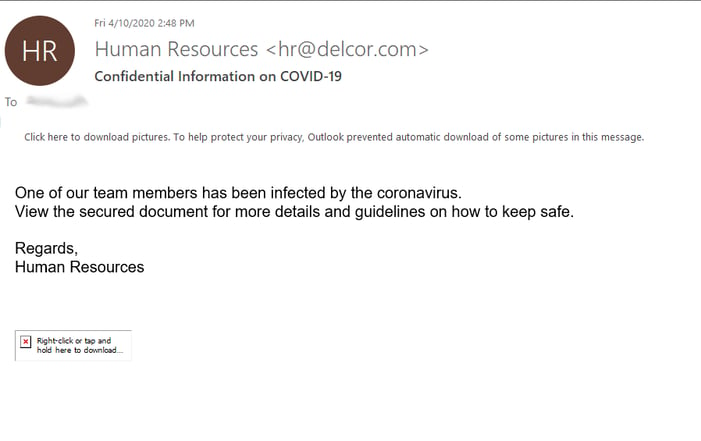
Keep Calm and Don’t Click the Link
Follow these tips to avoid COVID-19 social engineering attacks:
- Don’t donate without doing the proper research and never donate in cash, by gift card, or by wiring money. Follow this guide from the Federal Trade Commission to donate wisely and avoid charity scams.
- Ignore emails claiming to have new information about COVID-19, especially those claiming to have vaccinations or home test kits.
- Don’t respond to texts, emails, or calls about stimulus checks from the government.
- Pay particular attention to emails claiming to be from the Center for Disease Control (CDC) or World Health Organization (WHO).
- Keep calm. Cybercriminals take advantage of disasters because people are distracted and vulnerable. Think before you click and use common sense.
To learn more about protecting yourself and your organization from phishing attacks, see these blog posts: